Cryptographic Testing
Cryptographic Algorithm Testing
Consult our experts. We are happy to support you.
The NIST Cryptographic Algorithm Validation Program (CAVP) provides validation testing of Approved (i.e., FIPS-approved and NIST-recommended) cryptographic algorithms and their individual components. Cryptographic algorithm validation is a prerequisite of cryptographic module validation.
What atsec offers:
atsec US offers algorithm testing specified under the NIST Cryptographic Algorithm Validation Program (CAVP) through its accredited Cryptographic Security Testing (CST) laboratory (NVLAP Lab Code #200658-0); the list of cryptographic algorithms that can be tested by an authorized laboratory are listed on the CAVP web page.
atsec also provides full support for the NIST Automated Cryptographic Validation Testing System (ACVTS), including training your team to be proficient with the testing system maintained by NIST and providing guidance and know-how on using it. We can get you up to speed with the new vector format, newly testable ciphers, and querying the demo and production servers.
Authoritative websites:
More information:
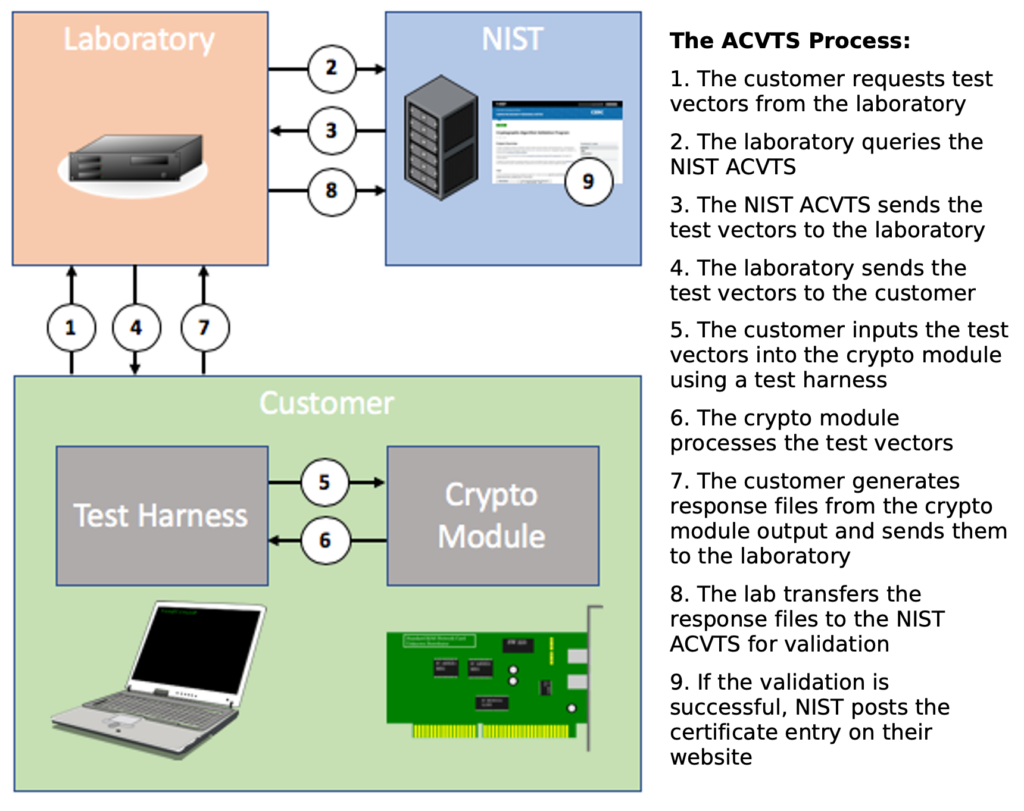
Why our services are important to you:
Testing whether cryptographic algorithms are implemented correctly is a prerequisite for FIPS 140-3 cryptographic module testing, NIAP Common Criteria evaluations, and by other select Common Criteria schemes and certification programs that accept the NIST CAVP certificate.
Vendors do have the option to access the ACVTS themselves, but that comes with a number of challenges, such as needing to dedicate resources to the project, knowledge of how to operate the tools, and an NVLAP accreditation. It is typically more efficient to outsource this effort to an accredited laboratory like atsec US’s CST lab.
To make the testing process as little of a hassle as possible, atsec created solutions to make the switch to the ACVTS easy and efficient for our customers, including the Automated Cryptographic Verification Protocol (ACVP) Proxy and ACVP Parser.
Downloads:
Further information for your certification journey.
Introduction to the
CMVP and CAVP
Watch our Introduction to the Cryptographic Module Validation Program and the Cryptographic Algorithm Validation Program video, which will provide you with a head start on understanding the certification process.

Still have questions?
Can’t find what you’re looking for? Let’s talk!
FIPS 140-3 Testing
FIPS 140-3 specifies requirements related to securely designing and implementing cryptographic modules, and compliance is increasingly mandatory worldwide.
Entropy Source Assessment
Documented conformance, where applicable, to the SP 800-90B is required by the CMVP for all FIPS 140-3 module validation submissions.
Common Criteria Evaluation
The Common Criteria (CC), also known as ISO 15408, is an internationally recognized standard used to specify and assess the security of IT products.
The Information Security Provider
Read Our Latest Blog Articles
Learn the latest and greatest about information security. You’ll find insights and analyses of recent developments in technology and policy on our blog.
-

CLAR 2025 & BLESS 2025: Twin Conferences at the Forefront of Logic, AI, and Ethics
The CLAR 2025 and BLESS 2025 conferences converged on a shared mission: tackle pressing challenges with formal logic.
-

Cybersecurity Testing Added to RED – atsec is on it!
The Radio Equipment Directive has new cybersecurity requirements that atsec is on top of!
-

CAVP Issues Updated Guidance on Algorithm Certificate Posting
CAVP has made it clear: just include facts in ACVTS data fields.
