-

Securing the Software Supply Chain
All components comprising a software product are ultimately the responsibility of the developer of that product, even if one or more of those components is supplied by a third party. This is especially true when the product is evaluated for Common Criteria (CC) certification. Recently, the National Security…
-

atsec became a PCI GEAR member again for 2022-2024
atsec China is pleased to announce that atsec has become one of the PCI Global Executive Assessor Roundtable (GEAR) members for the 2022-2024 term. atsec China has joined in PCI GEAR since 2018 during its initial establishment. In 2022, atsec China is one of 27 organizations to join…
-
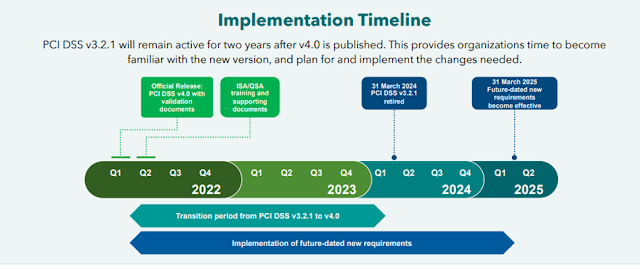
atsec Became One of the First PCI DSS v4 QSA Companies
atsec China (“atsec” for short in this article) has completed the training and examination on “PCI DSS QSA Version 4 Transition” provided by the Payment Card Industry Security Standards Council (PCI SSC) and became one of the first Qualified Security Assessors (QSA) companies globally to perform the assessment…
-
atsec virtually at the National Cybersecurity Center of Excellence
atsec is excited to have been invited to the virtual kick-off meeting for the “Automation of the NIST Cryptographic Module Validation Program” at the National Cybersecurity Center of Excellence (NCCoE). The National Institute for Standards and Technology (NIST) organized the kick-off meeting on June 1st of, 2022. It…
-

NIST Entropy Source Validation Server Available
NIST plans to offer a separate validation program apart from FIPS 140 to cover entropy sources: the ESV (Entropy Source Validation) program (hereafter ESVP). As part of the new validation effort, NIST recently launched an automated system to upload the required information in a structured manner: the Entropy…
-

atsec becoming first cybersecurity MetaLab
We are excited to announce that atsec information security has become the first IT Security Lab that has been accredited as a testing lab for the Metaverse. IT Security in virtual environments is as important as in the real world. While in the real world there are a…
-

New Cybersecurity Initiative will use Detection Dogs to spot Cyber Security Attacks to the US IT Infrastructure
Washington, DC—A new cybersecurity initiative dubbed PAWS (Puppy Assisted Warning Systems) has been introduced today by the US Department of Defense (DoD) to combat and deter the rising threat of cybersecurity attacks from countries who have vested interests to undermine US IT infrastructure and businesses. The 1.7 trillion…
-

atsec is recognized as a NESAS Security Test Laboratory to perform Security Evaluation of Telecommunication Equipment
The GSMA (Global System for Mobile Communications) organization recognizes atsec’s ISO/IEC 17025 accreditation that now allows network product evaluations against NESAS Security Assurance Specifications (SCAS). The NESAS scheme is a collaboration and jointly led by 3GPP and the GSMA, and is open to all vendors of network equipment…
-

Transitioning to NIST SP 800-56A Rev3: what you need to know
by Swapneela Unkule NIST SP 800-56A provides recommendations for Pair-Wise Key-Establishment Schemes Using Discrete Logarithm Cryptography. Diffie-Hellman (DH), Elliptic Curve DH (ECDH) and Menezes-Qu-Vanstone (MQV) key-agreement schemes are specified in this standard. These Key-Agreement Schemes (KAS) are widely used in network protocols such as TLS. The SP 800-56A…
