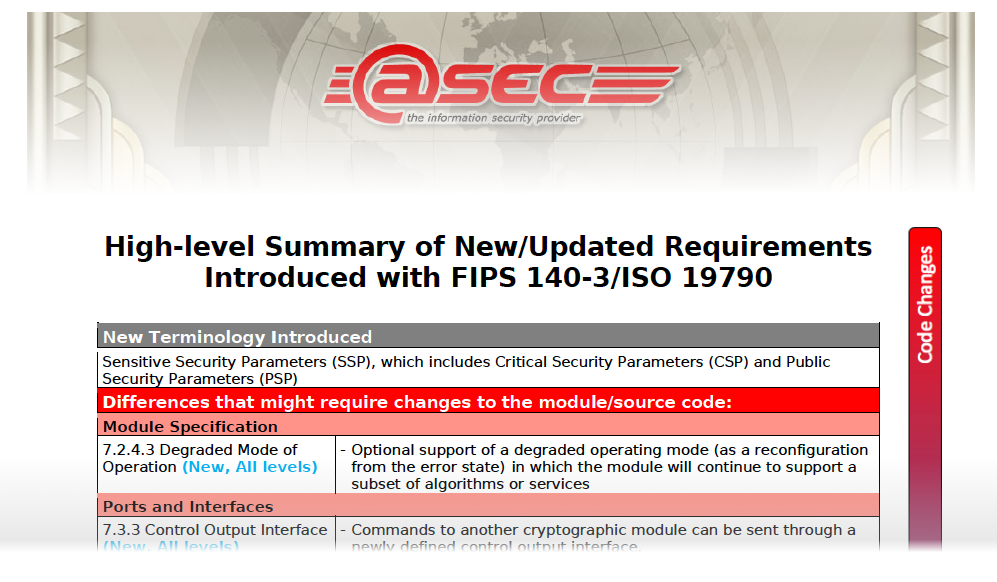
-

SP800-90A and SP800-90B compliant Linux Random Number Generator
Stephan Mueller With the enforcement of SP800-90B starting in November 2020, the noise sources behind the Linux /dev/random, /dev/urandom and the getrandom system call interfaces must comply with all requirements stipulated by SP800-90B. If this compliance is not achieved, all modules using Linux random number generator as entropy…
-

International Cryptographic Module Conference 2019 in Vancouver, Canada
After a day of pre-conference workshops, the 7th International Cryptographic Module Conference (ICMC) was kicked off this morning with a welcome address from atsec’s VP and Lab Director Yi Mao. (from left to right: Renaudt Nunez, Stephan Mueller, Fiona Pattinson, Swapneela Unkule, Yi Mao) Yi Mao’s Opening Speech…
-

Cryptographic module related work in ISO/IEC JTC 1/SC 27/WG 3
For several years the value of conformance testing against the FIPS 140-2 specification has been well accepted, and the assurance gained through validated conformance has been specified in several other markets.
-

How the U.S. government shutdown affects us
As many of our customers will be aware, the current U.S. government shutdown can affect their projects with atsec. This time, the partial shutdown includes the U.S. Department of Commerce, and hence NIST’s Computer Security Resource Center. This affects our customers with FIPS 140-2 conformance validations (CMVP), and…
-

International Cryptographic Module Conference 2018 in Ottawa, Canada
After a day of pre-conference workshops, the International Cryptographic Module Conference (ICMC) 2018 was kicked off this morning with a welcome address from atsec’s VP and Lab Director Yi Mao. The welcome was followed by keynote speeches from Jason Hart, CTO of Data Protection for Gemalto UK and…
-

Yi Mao’s Opening Speech at the Fifth ICMC
“Dear Community, It is the second time that I have had the honor and pleasure to open the International Cryptographic Module Conference. This year is very special since it is the fifth anniversary of the conference. I’d like to welcome you all with an image from the end…
-
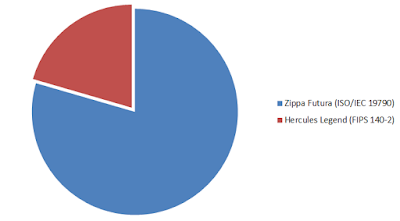
ICMC Presidential Debate
The votes have been counted and Zippa Futura and ISO/IEC 19790 win by a large margin:
-

Commercial Assurance of Cryptography in North America
Cryptographic Algorithm Validations The Cryptographic Algorithm Validation Program (CAVP) is an organization that is managed solely by the National Institute of Standards and Technology (NIST). Information about the CAVP scheme, including the official validation lists, can be found at NIST’s web page for the CAVP. The CAVP certifies…