The Information Security Provider
atsec IT Security Blog
News about Common Criteria, FIPS, Conferences
and other topics revolving around IT security.
For a non-paginated list of all of our blog posts, head over to our Blog Archive page.
-

atsec at the PCI Community Meeting 2023
atsec attended the 2023 PCI Asia-Pacific Community Meeting and presented on PIN security.
-

atsec at the International Common Criteria Conference 2023
atsec is attending ICCC once again – hope to see you at our booth or one of our sessions!
-

Cybersecurity Requirements for Medical Devices
The IEEE established a Medical Cybersecurity Certification Program, and atsec is the first IEEE recognized testing lab!
-

The 11th International Cryptographic Module Conference
We’re headed off to ICMC23, and we can’t wait to see everyone there!
-

Artificial Intelligence in Evaluation, Validation, Testing and Certification
AI is becoming increasingly prevalent and powerful – how is atsec planning to use it?
-

Entropy Source Validation (ESV) Certificate Issued for the Intel DRNG
Intel’s Digital Random Number Generator, used in many of its processors, receives an ESV certificate.
-
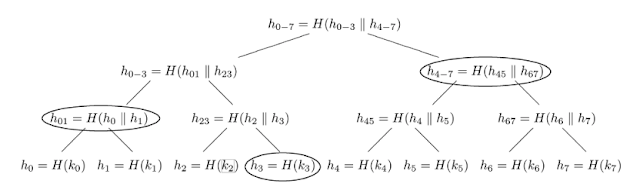
First Post-Quantum Algorithm Certificate Issued by CAVP
atsec obtained the first validation for a post-quantum cryptographic algorithm using the ACVP.
-
The IoT Security Global Certification Challenges
With IoT devices now integral to our lives, how will we protect the data they collect from cyber criminals?
-

CEST (Confidential Evaluation of Software Trustworthiness) project finished
The Confidential Evaluation of Software Trustworthiness research project has been completed!
