The Information Security Provider
atsec IT Security Blog
News about Common Criteria, FIPS, Conferences
and other topics revolving around IT security.
For a non-paginated list of all of our blog posts, head over to our Blog Archive page.
-

The genesis of atsec’s name, logo, and websites
When atsec was about to be founded, one of the first questions the founders (a German, an Italian, and a Swede) had was which name would best represent the company’s approach to information security, but more importantly, whether the domain would be available. Here is the list of…
-

atsec Scholarship Connects Logic and Cryptography
The two most repeated terms at the NIST Entropy Workshop held on April 27-29 are “mathematical model” and “justification.” That brought me back to my college days at Peking University where I first studied Mathematical Logic. Logic is all about valid rules of inference. Mathematical logic applies the techniques of…
-

New Cybersecurity Initiative will use Detection Dogs to spot Cyber Security Attacks to the US IT Infrastructure
Washington, DC—A new cybersecurity initiative dubbed PAWS (Puppy Assisted Warning Systems) has been introduced today by the US Department of Defense (DoD) to combat and deter the rising threat of cybersecurity attacks from countries who have vested interests to undermine US IT infrastructure and businesses. The 1.7 trillion…
-
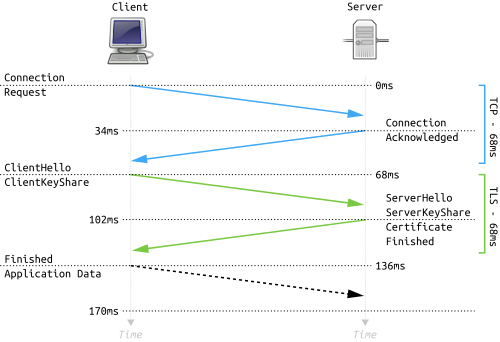
The Impact of TLS 1.3 and ACVTS on FIPS Certification Testing
by Marcos Portnoi, Stephan Mueller, and Viktoria Meyerhoff In 2018, the Internet Engineering Task Force (IETF) published RFC 8446, “Transport Layer Security (TLS) Protocol Version 1.3”, a new standard for the latest version of TLS. TLS is the successor of SSL (Secure Sockets Layer), which was developed by…
-

On Software Supply Chains
by King Ables The attack on the SolarWinds network management platform Orion allowed a bad actor to inject malware into the product prior to it being signed and deployed to customers during a regular software update. This highlights a largely underappreciated but universal truth of the Internet age–almost…
-

atsec is recognized as a NESAS Security Test Laboratory to perform Security Evaluation of Telecommunication Equipment
The GSMA (Global System for Mobile Communications) organization recognizes atsec’s ISO/IEC 17025 accreditation that now allows network product evaluations against NESAS Security Assurance Specifications (SCAS). The NESAS scheme is a collaboration and jointly led by 3GPP and the GSMA, and is open to all vendors of network equipment…
-

Happy Birthday atsec!
Today atsec celebrates its 21st Birthday! We can finally get a pilot license, gamble at the casino and we won’t be mad when we get carded at the ICMC! We are happy to look back on more than two interesting decades and would like to thank our customers,…
-

Holiday Greetings from atsec
Our colleagues from around the world wish you Happy and Healthy Holidays and a good start into 2021.

